Business requirement
With the development of the Internet, various security problems have become increasingly serious, seriously threatening the rights and interests of individuals and enterprises, but most security problems come from within enterprises. The computer is the most important tool for users to deal with business, and the access management of the computer can effectively improve office efficiency, reduce security risks, and enhance network security, thus creating more value for users. At present, most terminals are loosely managed, which mainly has the following problems:
■ Identity authentication of the terminal and whether the terminal is a legitimate user
■ A security event caused by an operating system vulnerability
■The system patch is not updated in time
■ Free access to peripherals, such as U disk, Bluetooth, etc
■ External personnel or third-party developers use mobile laptops to access the service private network or office network system without permission
■ Terminal security policies are inconsistent, affecting global security
Scheme overview
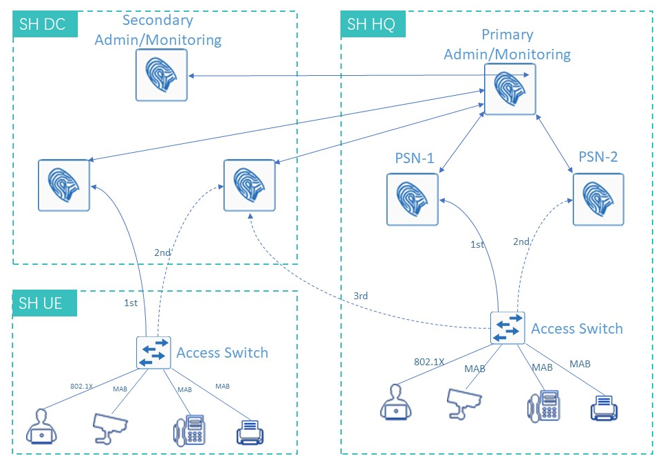
The Cultidome solution enables limited access to the Intranet to ensure Intranet access security and block unauthorized devices from accessing the Intranet. The basic principle is that the network switch recognizes the company's peripherals, IT equipment and user terminals through 802.1X, and releases and grants corresponding permissions. Non-default access permit devices must enter the application process and enter the wired Intranet only after the application is complete. The two hardware nodes serve as Admin and Monitoring nodes in the main equipment room and the DC equipment room of the headquarters. Data is backed up with each other. PSN nodes are VMS. Two PSN nodes are installed at the headquarters and load balancing is performed. PSN nodes are installed in the DC equipment room to back up the headquarters and UE PSN nodes.
Scheme value
■Centralized management
It provides an integrated security access management process from visitor management, identity authentication, security check, isolation and repair, access control to network access traceability, centralized management and monitoring of access devices, and forms an integrated terminal security solution with functions such as antivirus, desktop management and control, security audit, and security baseline
■ Strong adaptability to network environment
The off-line deployment mode does not change the user network architecture. Supports multiple authentication technologies, such as application access, Portal, 802.1x, policy-based routing, AD/LDAP, and wired and wireless authentication, meeting the deployment requirements of large-scale networks
■ Real name system unified authentication management
It supports the linkage authentication of multiple third-party servers, such as AD, LDAP, and Http, ensuring unified authentication management under the real-name system, making terminal access management secure, transparent, and controllable, and meeting information security management requirements
■ Integration of network access compliance inspection and repair
Support a variety of security check and repair behavior, isolate non-compliant terminals, and can be guided repair, repair successful access to the network, always protect the customer's access to the network security baseline, and provide constantly updated security check engine and rule base upgrade, with good scalability
■ Multiple Dr Modes
Supports multiple modes, such as hot standby (HA) and cold backup, to ensure that users are not affected and reliability is high

