Business needs
All walks of life are undergoing digital transformation, and the requirements for the stable operation of office information systems are getting higher and higher, but various security threats have an increasing impact on the stable operation of office systems. According to the results of a special cybersecurity survey conducted by the FBI and CSI, more than 85% of security threats come from within the company. The illegal intrusion of the office information system from outside the company, the malicious destruction of internal users and the security risks caused by the inadvertent cause make the security construction of the office information system full of holes, and enterprise users need to build a stable, safe and efficient office information system to provide a solid foundation for digital transformation.
In the current situation, the security threats faced by office information systems are:
■ The frequency of attacks has increased dramatically
■ Diversification of attack methods
■ New and unknown attack methods emerge one after another, and it is impossible to prevent them
■ Low visualization of the internal security threat status of the office system
■ Information leakage causes significant losses to corporate reputation and economy
■ Information security management and operation and maintenance work is heavy, and personnel pressure is high
Overview of the scenario
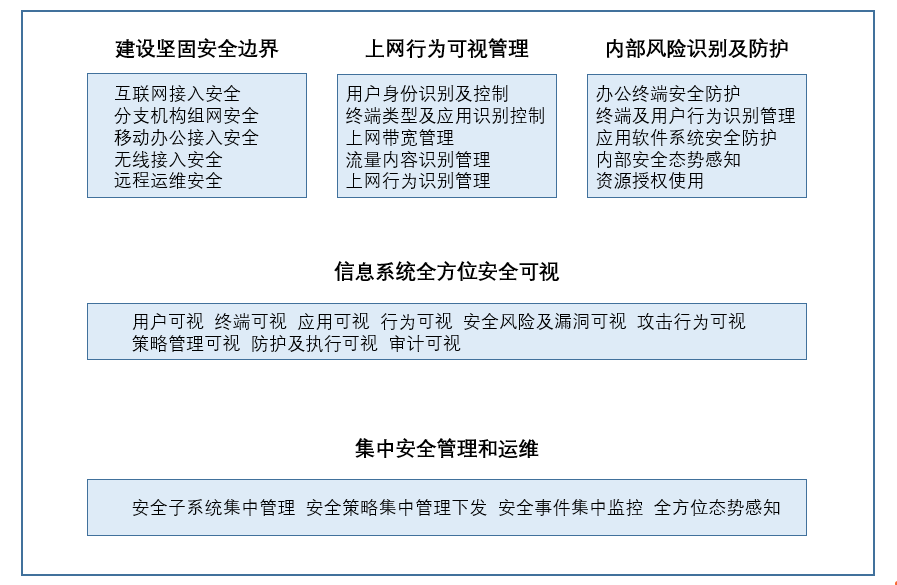
The office information system security solution improves the security defense level of the office information system in an all-round way on the basis of the security visualization of the entire information system, focuses on strengthening the ease of use and efficiency of information system security management and operation and maintenance, and creates a stable, safe and efficient office information system, providing a solid foundation for digital transformation.
Realization and value of the solution
■ Build a solid security boundary of the office information system, reduce the number and exposure time of security vulnerabilities, and reduce the use channels of external attacks
■ The online behavior of users in the office information system can be monitored and controlled, so as to improve the office efficiency of employees, avoid compliance risks, avoid data leakage, and ensure security
■ Identification and protection of internal security risks in the office information system, so that the office information system can realize the full life cycle protection, and the user terminal is also protected
■ The all-round security visualization of the office information system helps users quickly and timely discover security threats, and realizes the all-round security situation awareness, control and management of the office information system
■ Centralized security management and operation and maintenance reduce the complexity of office information system maintenance and management, and reduce the work pressure of operation and maintenance personnel

